 General counsel, IT professionals and CEO’s frequently lose sleep worrying about data security, including email security. Worldwide, people send approximately 205 billion emails each day! The average business user sends and receives 125 emails. Today, businesses rely on email for the majority of their communications, including those transmitting sensitive information.
General counsel, IT professionals and CEO’s frequently lose sleep worrying about data security, including email security. Worldwide, people send approximately 205 billion emails each day! The average business user sends and receives 125 emails. Today, businesses rely on email for the majority of their communications, including those transmitting sensitive information.
Email was developed when the internet was a much smaller place. At that time, its inventors never intended that email become the primary form of business communication. As such, email security was not a concern.
A brief explanation of the internet illustrates why email is so vulnerable. During transmission, an email encounters multiple points of vulnerability along the internet. Once you hit the send button, your email travels through a series of switches and routers, likely owned and operated by different entities. Hackers can read your email if only one of these points is not secure. Scary stuff!
Consider how many of your emails contain sensitive information. For example, emails with outside counsel frequently contain non-public information about publicly-traded companies. Emails in employment cases often contain personally identifiable information or personal healthcare information. Hackers relentlessly pursue this type of information.
Now that you are properly frightened, what can you do? Short of instituting a system that encrypts all of your email with outside counsel, there are three easy ways that you can better secure your email.
3 Easy Ways to Improve Email Security
- Do not include sensitive data in the body of an email. Instead, include it only in an attachment, encrypted with a password. Microsoft Office makes it easy to encrypt documents. You simply go to File>Info>Protect Document and select Encrypt with Password. Next, create a password and press enter. You have now encrypted your document!
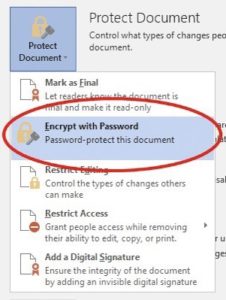
How to encrypt a Microsoft Office document with a password. Be sure to then send the password to the recipient in a separate email or, preferably, by voice or text. Otherwise, including the password in the same email as the attachment defeats the purpose of encryption!
- Encrypt PDF’s in Adobe Acrobat before sending them by email. To do this, open the PDF and choose Tools>Protect>Encrypt>Encrypt with Password. If you then see a box asking whether you want to change the security settings on the document, click yes. Next, click the box labeled, “Require password to open the document.” Then, enter a password at the top of the encryption box.
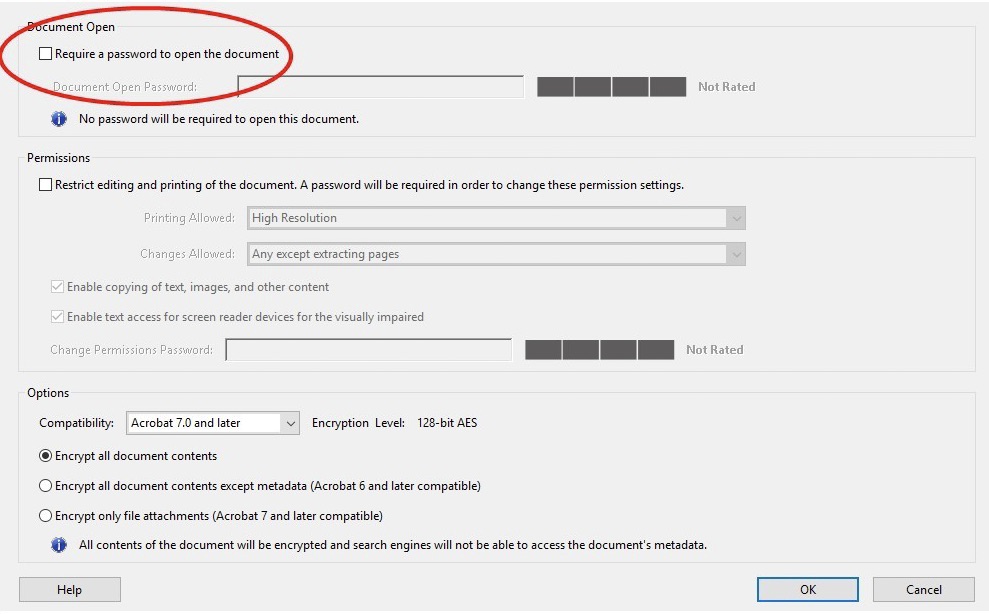
How to encrypt a PDF document with a password in Adobe Acrobat. - Although not as secure as encryption, a final method for securing a document sent by email is to zip the document and require a password to open the zip file. A variety of low cost or free programs are available online to add this feature. This approach does not provide encryption, but it is more secure than sending the document without any protection.
No method provides foolproof security. Nonetheless, a little effort goes a long way to protecting your sensitive information and helping you sleep better.
Photo courtesy of Christoph Scholz on Flickr.


 For the first time in weeks, you slept well last night, confident that your expensive consultant found every hole in your company’s data-security program. The board of directors was thrilled with your report on the robust, new data-security policy that you personally approved. But, did your consultant look deep enough? Did she realize that although your company encrypts emails containing personally identifiable information, one of your vendors does not encrypt their responsive emails containing the same information? Did she understand your business well enough to realize that a service provider collects and stores customers’ personally identifiable information on its servers through the app it designed for your company?
For the first time in weeks, you slept well last night, confident that your expensive consultant found every hole in your company’s data-security program. The board of directors was thrilled with your report on the robust, new data-security policy that you personally approved. But, did your consultant look deep enough? Did she realize that although your company encrypts emails containing personally identifiable information, one of your vendors does not encrypt their responsive emails containing the same information? Did she understand your business well enough to realize that a service provider collects and stores customers’ personally identifiable information on its servers through the app it designed for your company? arefully consider what information they actually needed.
arefully consider what information they actually needed. There once was a time when in-house lawyers could sleep soundly and let the computer experts stay up at night worrying about IT issues. Those days are long gone (if they ever really existed at all)!
There once was a time when in-house lawyers could sleep soundly and let the computer experts stay up at night worrying about IT issues. Those days are long gone (if they ever really existed at all)!