
If holiday parties and New Year’s Eve were not enough to keep you up at night, the State of Maryland has given businesses a hangover that will last long beyond the holidays. Effective January 1, 2018, Maryland’s amended data privacy law imposes new requirements on businesses. The State says these new requirements may create a “potential[ly] meaningful” financial impact on Maryland businesses.
I am not going to detail all of the changes to the law in this post – look for them shortly. However, below are a number of areas that businesses need to be concerned about going forward.
Important Maryland Data Privacy Provisions
- A “breach” no longer requires access of the personal information. Now, it only requires acquisition of that data, regardless of whether someone actually accessed them. This is potentially an important change, as it broadens the instances when a business must give notice.
- The definition of “Personal Information” has been expanded.
- Maryland businesses must “implement and maintain reasonable security procedures and practices.” However, when amending the law, the Maryland General Assembly refused to adopt a definition of this phrase for guidance. Thus, businesses must continue to monitor changes in both technology and the law, as courts and regulators will likely evolve their definitions over time.
- A business cannot delay acting when faced with a potential breach. Businesses must give notice of a breach as soon as practicable, but in no event later than 45 days after discovering the breach. Notice must now be given when the breach “creates a likelihood that personal information has been or will be misused.”
- The law has altered how notice of a breach may be given to an individual, in certain instances.
- The law applies to customers, as well as employees and former employees.
- Businesses that disclose personal information to unaffiliated third-party service providers must contractually require that these service providers implement and maintain reasonable security procedures and practices.
The risk of non-compliance can be expensive. So, if you want to sleep better this year, stay on top of Maryland’s amended data privacy law. Spending a few dollars now may save you a small fortune in the future.

 General counsel, IT professionals and CEO’s frequently lose sleep worrying about data security, including email security. Worldwide, people send approximately 205 billion emails each day! The average business user sends and receives 125 emails. Today, businesses rely on email for the majority of their communications, including those transmitting sensitive information.
General counsel, IT professionals and CEO’s frequently lose sleep worrying about data security, including email security. Worldwide, people send approximately 205 billion emails each day! The average business user sends and receives 125 emails. Today, businesses rely on email for the majority of their communications, including those transmitting sensitive information.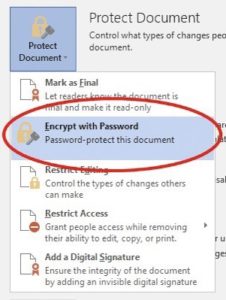
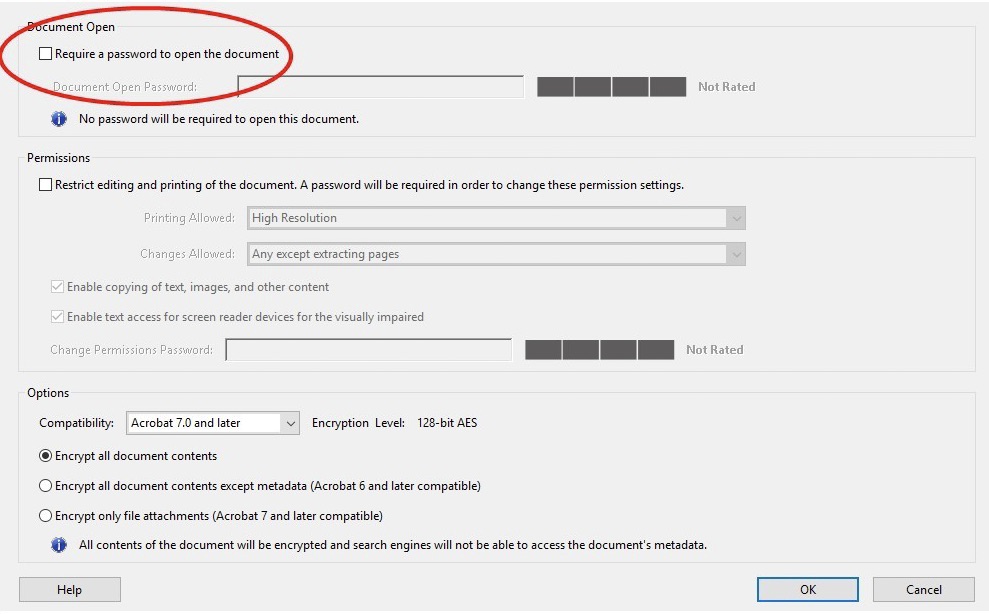

 For the first time in weeks, you slept well last night, confident that your expensive consultant found every hole in your company’s data-security program. The board of directors was thrilled with your report on the robust, new data-security policy that you personally approved. But, did your consultant look deep enough? Did she realize that although your company encrypts emails containing personally identifiable information, one of your vendors does not encrypt their responsive emails containing the same information? Did she understand your business well enough to realize that a service provider collects and stores customers’ personally identifiable information on its servers through the app it designed for your company?
For the first time in weeks, you slept well last night, confident that your expensive consultant found every hole in your company’s data-security program. The board of directors was thrilled with your report on the robust, new data-security policy that you personally approved. But, did your consultant look deep enough? Did she realize that although your company encrypts emails containing personally identifiable information, one of your vendors does not encrypt their responsive emails containing the same information? Did she understand your business well enough to realize that a service provider collects and stores customers’ personally identifiable information on its servers through the app it designed for your company? arefully consider what information they actually needed.
arefully consider what information they actually needed.